Background
A large Education Technology company sells educational products and services directly to high school and college students. That includes renting textbooks, guiding customers in their search for scholarships, and offering online tutoring.
In the course of its business, the company collects a treasure trove of personal information about many of its customers, including their religious affiliation, heritage, date of birth, sexual orientation, disabilities, and parents’ income. The data gathered as part of its scholarship search service is “very sensitive.”
While the company took steps to have the right set of staff and tools to take care of security related to the data, the high alert volume of security incidents, the growth of the company, the use of consultants, and security practices around them made it susceptible to a breach. Additionally, the non-IT staff in the firm wasn’t very security aware which often led to security incidents like data breaches, phishing attempts, and ransomware attacks being successful.

THE CLIENT
Education Technology Company
REGION
USA
TYPE OF WORK
IT & security Operations
INDUSTRY
Education
MAIN TECHNOLOGIES
Automation Units, Integrations, Decision Units, Workflows
Key Challenges

Alert Volume
High volume and frequent alerts related to storage configurations, user access and control changes.

Human Factor
Lack of experience in security awareness of non-IT staff and the deficiency of qualified specialists who are able to handle security incidents.

Service Requests
Not able to meet user requirements due to the non-availability of the storage assets, user access updates and control configuration changes.

The need for Integrations
Number of applications using the storage is huge along with both internal and external use of the applications and storage data. Users and access need to be managed on a continuous basis.
Work Process
The customer has a large cloud footprint and has assets in multiple regions with multiple cloud accounts. They are using cloud security tools like Guard Duty and Security Hub for alerts and ITSM for event tracking with Teamwork for approvals.

Solution
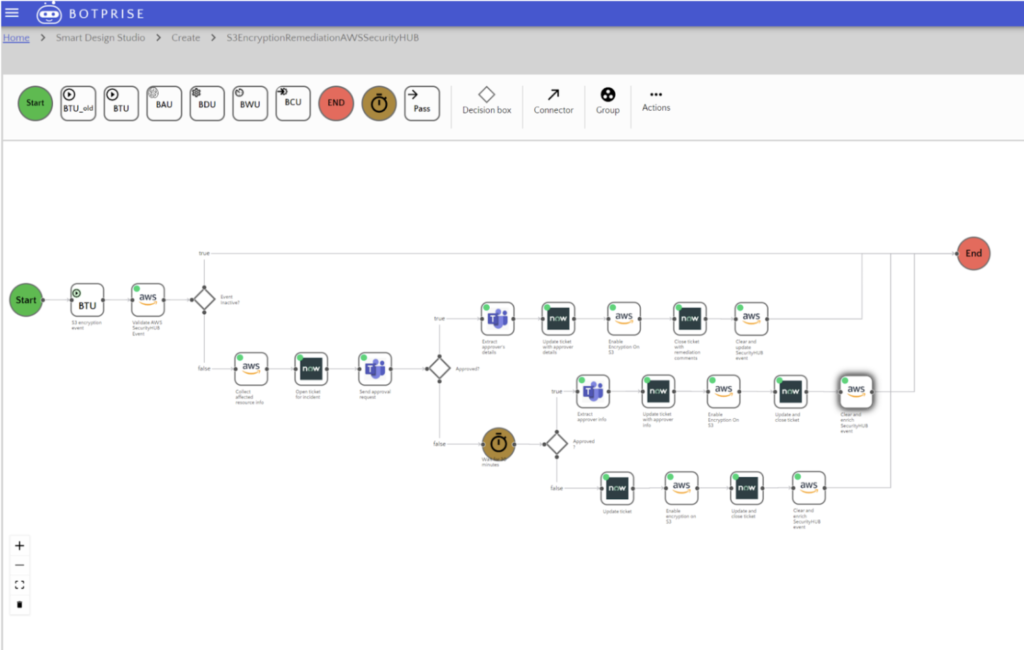
The Botprise Solution, with its integration capabilities into the security tools, cloud assets for storage, user management, tracking and control, ticketing system and teamwork for collaboration was able to create a smartbot that would look at security alerts. Furthermore the alerts were automatically checked for required security controls and remediation flows automatically triggered off with collaboration over teamwork for approval steps. A high level workflow representing the modeled process is as shown below:
The EdTEch company now has a solution to automatically manage misconfigurations to maintain desired cloud security posture, deploy changes to the existing process or develop new processes on a single platform regardless of the tools that are required to be integrated.

Outcome
The firm is now able to deploy an event based, data-driven security solution for misconfigurations and perform automation that has helped it reduce its attack surface substantially. Furthermore, more automations have been deployed that address other security alert scenarios.
Botprise’s Smartbots now spearhead various related processes as a digital agent that takes on security alerts and completes the tasks with improved and consistent responses regardless of the volume or frequency of these alerts. The IT staff are now able to focus on business-impacting operational issues thereby improving the overall security of the firm and time to resolve.

Optimization? Improvement? Automation?
Do you want to optimize your product or learn how you can comfortably manage your business? Write to us!

Lead time reduction by 95%

90% reduction in workload for existing security and IT staff

90% reduction in the security incidents across the firm


